Do I Need An Antivirus Software On Mac
- Do I Need Antivirus Software On My Mac
- Do Macbooks Need Antivirus Software
- Do I Need Antivirus Software On Mac
- Do I Need An Antivirus Program On My Mac
- Do I Need Antivirus Mac
Do You Need Antivirus Protection On Your Mac?
Do I Need Antivirus Software On My Mac
Do Macs need antivirus software? That very much depends on who you listen to. Last week, I asked my Mac-owning Twitter followers if they used security software on their Macs. The answer was an overwhelming ‘no’.
Do Macbooks Need Antivirus Software
Often you will hear claims that Macs don’t get viruses, and that there is no reason for antivirus protection software on the Mac platform. However with the increase in Macs on the market, and the increase in using peer-to-peer services, Macs are at a greater risk than they ever have been in the past.
Only 50% of Mac users are running virus protection when compared to the 76% of Windows users. Also, 65% of the virus protection on the Mac platform is not real-time protection, which means that the software needs to be run manually to be effective, while on Windows systems the real-time usage is 61%; almost the opposite of the Mac.
With OPSWAT reporting in 2015 that 97% of users using antivirus protection or malware protection software have not run a scan in the last 7 days, it shows how important it is to get a malware protection that offers live protection.
Apple mac weather station software for raspberry pi. It is true that there are fewer viruses and malware on the Mac platform, but the main reason there are fewer viruses on a Mac than a PC is because it is more profitable to create a virus for a Windows based system. A Windows virus will affect more users, businesses, and organizations, as well as allow the hacker to gain access to more information.
With Macs becoming more commonplace in and out of the workplace, hackers are starting to develop attacks specifically for the Mac platform. Whether to attack the Mac itself, or to lie dormant until a Windows based system can be infected.
What Is Malware And Why Should I Care?
Malware, or Malicious Software, is used to either gather information or gain access to your system or network. Malware is a term that was coined in the early 90s to incorporate all forms of computer attacks, as opposed to simply referring to them all as computer viruses, because different types of attacks worked in completely different ways and often times with vastly different motives.
Malware can come in many different forms, but some of the most common are:
Viruses
Worms
Adware
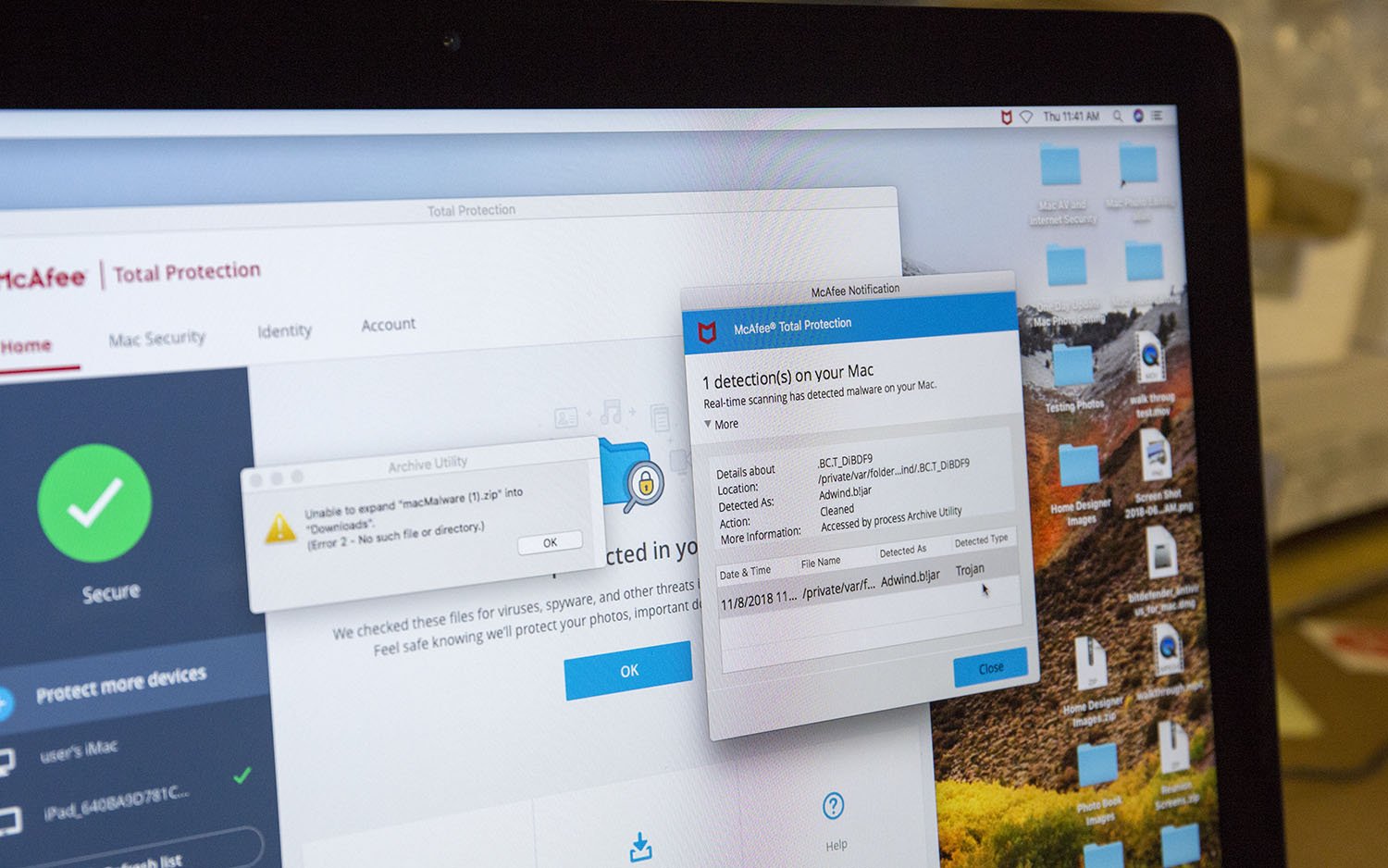
Trojan
Rootkits
Ransomware
Each type of malware will infect your system in a different way and use different tactics to stay active on your system and undetected as long as possible.
A Virus is normally hidden within another program or file that will attempt to replicate itself in an attempt to destroy data and corrupt your system. However a virus does require some human interaction to work. The virus will only start to replicate when the file that contains it is moved or opened. Viruses are often built with the intent of destroying your machine, and not so much for monetary gain or data collection.
A Worm behaves similarly to a virus, however there is one key difference: a worm will not require any human interaction. It is a standalone program and is not imbedded into another program. This means that the worm can replicate itself within your system with no human interaction or help. The worm will replace itself in an attempt to destroy data and corrupt the system.
Adware is the type of malware with which the majority of users are most familiar. Adware is what will automatically display advertisements while you are online, and often these ads are unwanted and unwarranted. In the early years of the Internet, popup ads were everywhere, constantly slowing down websites while serving as a perfect way for hackers to infect your system if clicked.
Even when these adware are not used for intentionally malicious purposes, hackers will input different types of viruses, worms, rootkits, or trojans that will then gain access to your computer.
The way you are shown advertisements when online is a bit complicated. An algorithm will provide the most catered ad to you based off of your search history. This means if you spent the last few days looking up different types of barbeques, you are most likely about to start seeing barbeque ads across every website you visit. This is because as you are searching for information online, different tracking cookies are being saved that monitor your search history specifically to create more targeted ads.
Unfortunately, the way a majority of large websites work is that they will pull their ads from an ad database, so the website will have no way of knowing which ad you are being shown. This has created a perfect way for hackers to infect user’s machines by placing worms and viruses in the ads themselves. Any website that uses an advertisement database is putting all of their users at risk. If you ever receive the message requesting that you turn off your adblock for specific websites, I would not recommend it. This is why we suggest using an ad blocker when online to help keep you safe from potential attacks.
A Trojan horse attack, more commonly referred to just as a Trojan, is a type of attack that will attempt to appear as a useful or needed utility or software to get a user to download the file. A Trojan attack gets its name from the Ancient Greek story of Greek soldiers sneaking through the walls of Troy in a gifted wooden horse statue, and the Trojan malware will behave the same way. To help keep you protected from Trojan attacks you only want to download files from reputable websites or from individuals you know, and do not click on any links in spam emails. In addition, many antivirus softwares offer the ability to quickly verify single downloaded files, so you can quarantine and verify a file is safe before opening.
A RootKit is a tool used by different types of malware to help keep itself contained and to avoid detection by the operating system or from a virus protection software. The RootKit will modify the operating system so that malicious activities do not show in your system processes list and keep its files from being read. RootKits have started to become more common in the malware world as more and more malware is being written with the intent of siphoning data from the system it is installed upon to either steal trade secrets or make monetary gains.
A Ransomware attack is an extremely nefarious type of malware, which will essentially lock your computer and demand a ransom in order for the hacker to release your computer and data. One of the most powerful versions of malware that was utilizing a RootKit were the ransomware attacks that started to show up more commonly at the beginning of 2016. A ransomware attack normally will start with either a social engineering attack or through the use of another malware attack such as a Trojan.
Social engineering, when it comes to the computer world, is to get someone to do something that grants you access to his or her system or database. This can be as simple as a co-worker asking you to login so that they can print something, or from receiving an email from a Nigerian prince asking for your banking information so he can send you money. Since a social engineering attack relies on the user offering up their information, it is not considered a malware; but is still one of the most effective ways at gaining unwarranted access to a system.
Once the ransomware has been installed on your system, a Rootkit will help hide its identity from your computer and any security features. After being hidden in your system, the ransomware will start encrypting your data without your knowledge. In some cases the ransomware will be active on a user’s system for well over a month before it presents them with the infamous ransomware notification.
Not all ransomware will look the same, or accuse you of the same activities, but the thing they will all have in common is asking for compensation to release your computer back into your control. Unfortunately once your data has been encrypted, and you do not hold the passkey, there is no way to get your data back without paying the fine.
The recommendation from the FBI is to pay the ransom and to hope they return your computer’s control, however the reality is just because you pay the fine does not mean your computer will be decrypted. You are just hoping the hacker’s word is good.
With Prosoft Engineering being primarily a data recovery company we did have to deal with a few customers who were dealing with ransomware, and unfortunately had to turn them away as we could not break the encryption. The only way to keep yourself safe from these types of attacks is to be sure you have a valid backup strategy.
Do I Need Antivirus Software On Mac
Is Malware Becoming More Common?
Unfortunately the image of a hacker is changing, less and less of these attacks are being developed and ran by individuals at home and more are being supplied as a malware service. This means you can purchase attacks that you can then run on random individuals with almost no programming knowledge.
This has lead to a huge increase in malware as a whole, roughly a 56% increase as reported by TrendMicro, but the largest increase in use was specifically with ransomware. The widespread use of ransomware was the result of malware being a service. Ransomware kits started to appear online for as little as $100 and would allow someone to extort thousands of dollars from unsuspecting users with nearly zero effort.
Ransomware kits were being used so frequently that Trend Micro reported an increase of 172% in ransomware attacks in 2016, also showing that 80 new ransomware ‘families’ were found, an increase of 752% from the previous year. This increase resulted in ~37% of United States organizations feeling the effects of a ransomware attack in 2016.
How Can I Protect My Mac?
There are a few steps that you can take that will help keep your identity and data safe while online.
As stated above, one of the common attacks is a form of social engineering. Most of the time this will be done through a phishing email which will ask for your login information for your bank or other sensitive accounts. In order to stay protected you want to make sure you are only opening emails from reputable sources that you know, and only entering your private information in safe, secure locations. If you are unsure if the email is legitimate, we recommend not opening the email and reaching out to the individual or company you believe the message to be from to verify.
While only clicking on and opening from known sources will help keep you safe online, it is not a failsafe. To ensure that your identity and data stays secure online you will want to be using a live antivirus scanner that will monitor new files being installed on your system to check for potential vulnerabilities. In the upcoming release of the newest version of Drive Genius, we are introducing a live Malware Scan that will work in tandem with the Drive Pulse utility to monitor all new downloads and keep you safe while you’re online.
Do I Need An Antivirus Program On My Mac
We recommend using antivirus for your Mac in conjunction with an automated backup system to keep your data as safe and secure as possible. Data Backup can now perform automated backups and send text and email notifications upon the completion or failure of the backups. With automated backups, you never need to worry about your backup being out of date.
About the Author
Do I Need Antivirus Mac
My name is Matthew and I am a Technical Support Representative for Prosoft Engineering as well as our sister company, The Data Rescue Center. I am a people person and it is my passion to help others successfully use, and maximize the potential of their hardware and software.